When CRA Compliance Roadmaps Meet M&A Due Diligence
In our previous article, we showed how a CISO’s CRA compliance roadmap looked perfect on paper until someone asked: “Can your products actually do this?” We revealed five questions that expose the gap between documentation and technical reality. Those questions matter most when buyers start examining your products during M&A due diligence.
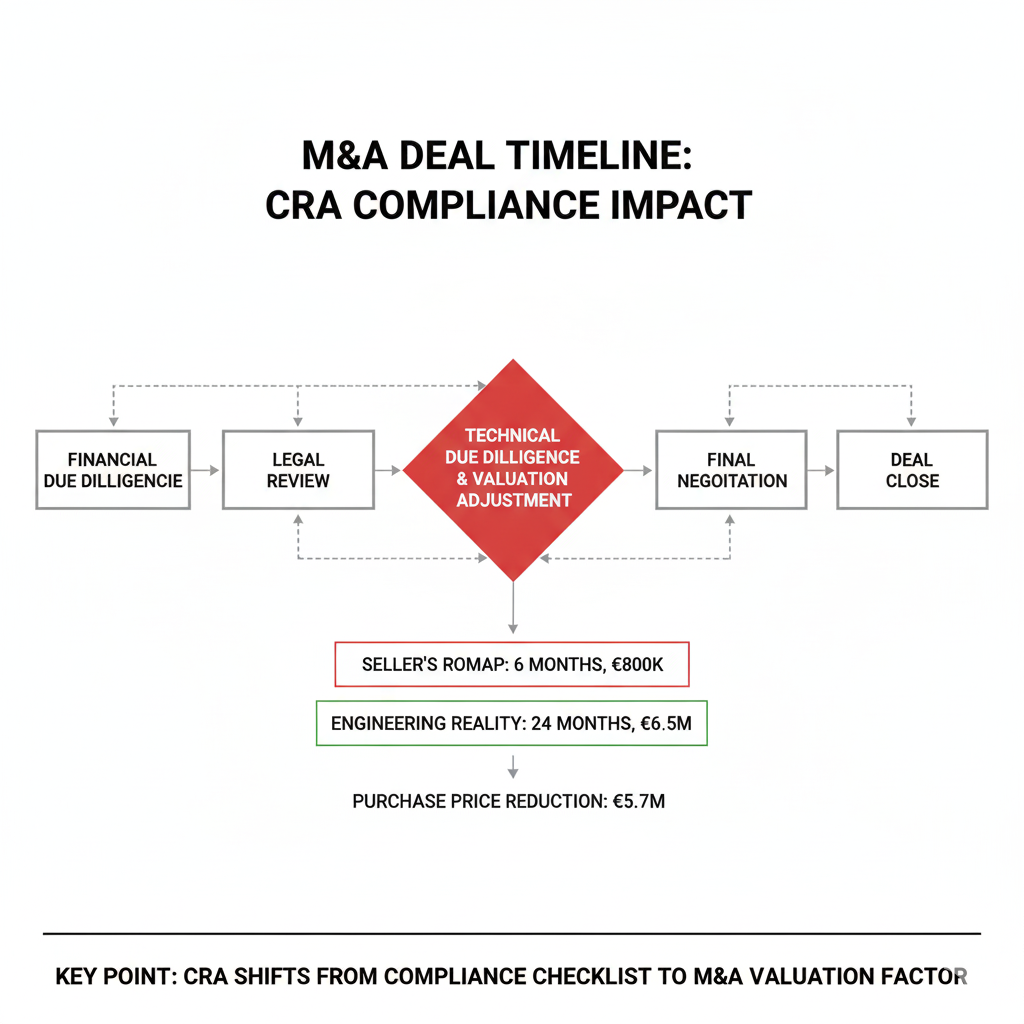
A private equity firm called us three weeks before closing a medical device acquisition. They’d completed financial due diligence. Legal review was done. The seller’s CRA compliance roadmap showed six months to certification with a budget of €800K.
Everything looked ready to close.
Then the buyer’s technical team asked one question: “Show us this actually works in your products.”
We spent two days with the engineering team. The devices were connected. Updates were technically possible. But the mechanism required clinical staff to physically access each device during scheduled maintenance windows.
No remote distribution. No automation. No way to push emergency security patches across their deployed base.
The compliance roadmap said updates were “supported.” Technically true. What it didn’t reveal: the product architecture couldn’t meet CRA requirements for timely security update distribution.
We showed the buyer what fixing this would actually require. Hardware revisions for future products. Field upgrade programs for 40,000 deployed units. New distribution infrastructure with cryptographic signing and verification.
Real timeline: 24 months. Real cost: €6.5M.
The seller’s roadmap: 6 months, €800K.
The deal closed. The purchase price dropped by €5.7M to account for actual remediation costs.
From Compliance Programs to Deal Economics
→ Key Point: In the past year, CRA shifted from compliance checklist to M&A valuation factor
Twelve months ago, M&A due diligence asked: “Does the target have a CRA compliance program?”
Today it asks: “Can their products technically comply?”
The difference matters. Compliance programs describe what should happen. Product architecture determines what actually can happen.
We’ve conducted technical assessments on 11 acquisition targets in the past six months. Eight required valuation adjustments. The pattern repeats consistently.
Compliance teams build solid programs. Documentation is thorough. Consultants validate the roadmaps. But nobody examines whether the products can technically execute what the documentation promises.
An industrial controls manufacturer was being acquired by a European conglomerate. Impressive compliance setup. Cross-functional steering committee. Quarterly compliance reviews. Big Four consultant engaged. Their CRA roadmap projected nine months to certification.
We asked the same question from Part 1 of this series: “When a critical vulnerability is disclosed, how quickly can you identify which product variants are affected?”
Their SBOM existed. Maintained in spreadsheets by two engineers who updated it manually “within two weeks, sometimes a month when busy with other priorities.”
→ Key Point: CRA Article 11 requires manufacturers to maintain and make available up-to-date technical documentation including SBOM
When the Log4j vulnerability hit, it took them six days to determine which products were affected. They had to contact vendors, wait for responses, manually cross-reference component versions, then validate which product configurations used affected libraries.
Six days to answer a question the CRA expects answered in hours.
Building the automated SBOM system they actually needed: €400K and four months of engineering work. Their compliance roadmap had allocated €50K for “SBOM documentation improvements.”
The buyer found this gap in technical due diligence. The €350K delta became a price negotiation point.
This is the pattern we described in Part 1. Roadmaps estimate documentation effort. Technical assessment reveals engineering reality.
Three Ways Gaps Become Deal Terms
→ Key Point: CRA compliance gaps impact M&A transactions through price adjustments, earnout conditions, and indemnification claims
1. Valuation Adjustments
A control systems vendor’s compliance roadmap estimated €1.2M over nine months to achieve CRA certification. We reviewed their actual products and found capabilities the roadmap assumed existed.
Automated SBOM generation: didn’t exist, just documentation of what should be built.
Vulnerability handling process: no documented triage workflow, no response timeline commitments, just a security email going to IT support.
Update distribution infrastructure: could generate updates but couldn’t securely distribute them, verify installation, or monitor deployment status at scale.
We quantified actual remediation. Automated SBOM integration into build pipeline: €400K. Vulnerability handling infrastructure with dedicated security resources: €300K annually. Secure update distribution with cryptographic signing and deployment monitoring: €800K.
Total: €2.3M over 14 months.
The seller’s roadmap: €1.2M over 9 months.
Purchase price adjusted by €1.8M to account for the gap between roadmap and reality.
The seller protested. Their Big Four consultant had validated the roadmap. True. The consultant had validated that compliance documentation existed and processes were described. They hadn’t validated that products could technically execute those processes.
2. Earnout Structures Tied to Actual Certification
A sensor manufacturer sold with earnout payments tied to CE marking milestones. €3M upon Year 1 certification for primary product line. €2M upon Year 2 certification for full portfolio.
→ Key Point: CRA Article 47 establishes conformity assessment procedures required before placing CE marking²
The seller was confident. They had 18 months of compliance work completed. Their consultant projected CE marking within six months.
We found architectural gaps in their update mechanism that the roadmap hadn’t accounted for. Products deployed in critical infrastructure needed secure remote update capability. Current architecture required manual on-site updates.
Remediation required redesigning the update distribution system, implementing cryptographic verification, and testing across their deployed base. Actual timeline: 12 months, not 6.
The seller missed the Year 1 earnout milestone. CE marking was achieved in month 14. The €3M payment wasn’t triggered.
The seller had done everything their compliance program required. But the earnout was tied to actual regulatory certification, not compliance effort or program completion.
3. Warranty Claims and Post-Close Indemnification
A control system vendor was acquired with standard compliance warranties in the purchase agreement:
“Seller represents that products comply with all applicable regulations including EU Cyber Resilience Act requirements.”
The warranty was provided in good faith. The seller’s compliance team believed they were compliant. Their consultant had reviewed the program. Documentation was comprehensive.
Post-acquisition technical audit during integration planning discovered gaps between warranty claims and product reality.
→ Key Point: CRA Article 14 requires manufacturers to establish processes for handling vulnerabilities and providing security updates³
No documented vulnerability handling process despite CRA requirements for coordinated disclosure timelines.
No security update distribution mechanism for products deployed three or more years ago.
No component-level SBOM capability despite product-level component documentation.
The buyer filed indemnification claim: €2.1M for remediation costs and delayed product launches while compliance gaps were addressed.
The seller’s defense: “Our compliance consultant validated our program. We relied on professional guidance.”
The buyer’s position: “The warranty was about product compliance capability, not program quality. Your consultant reviewed documentation. They didn’t validate products could technically comply.”
Claim settled at €1.6M. The seller’s consultant professional indemnity insurance covered nothing. The consultant had delivered what was contracted: documentation review and roadmap development. They hadn’t warranted technical capability.
What Technical Due Diligence Actually Examines Now
→ Key Point: M&A technical due diligence now validates product capabilities, not just documentation completeness
Buyers are no longer accepting compliance roadmaps at face value. Technical due diligence now includes the same validation questions we outlined in Part 1.
When we conduct CRA technical assessment for acquirers, here’s what we examine:
Product Architecture Validation
Not documentation review. We examine actual products. Test update mechanisms end-to-end. Validate cryptographic implementations. Verify the architecture can support CRA requirements under operational conditions.
SBOM System Demonstration
We don’t ask if you have SBOM documentation. We request real-time generation for three random product variants. We time how long it takes. We verify it’s automated, not manually compiled. We check if the system can answer vulnerability queries: “Which products contain component X version Y?”
If the answer requires engineers to compile data manually, the system doesn’t meet CRA operational requirements.
Vendor Contract Analysis
We pull contracts with the top 15 component suppliers. We search for specific security obligations. Most vendor contracts signed before 2023 contain standard commercial terms but no security update commitments, no vulnerability notification requirements, no patch availability timelines.
→ Key Point: CRA Article 13 requires manufacturers to provide security updates for expected product lifetime or 5 years minimum⁴
When vulnerabilities affect vendor components, the manufacturer’s CRA obligations don’t pause because vendors aren’t responsive. If your contracts don’t require vendor cooperation, your compliance depends on vendor goodwill.
Vulnerability Response Process Testing
We submit a simulated vulnerability report through the manufacturer’s disclosure process. We observe the triage workflow. We measure response timeline. We validate whether disclosure procedures can meet CRA timelines.
If the vulnerability report goes to a general IT inbox with no defined triage process, the manufacturer can’t meet Article 14 requirements.
Update Distribution Capability
We ask for demonstration of security update distribution to deployed products. Not theoretical process description. Actual demonstration. We measure deployment timeline. We verify installation verification exists. We check rollback capability if updates fail.
The assessment takes two to three days of product team time. The findings directly affect deal valuation and terms.
The Proactive Approach That Works
→ Key Point: Sellers who conduct technical assessment before M&A avoid valuation surprises
We worked with a sensor manufacturer preparing for sale. Six months before engaging buyers, they ran internal technical assessment using the framework from Part 1.
They found gaps. €1.8M in remediation costs. Ten month timeline to address architectural limitations in their update distribution system and automate their SBOM generation.
Instead of hiding this, they disclosed everything in their information memorandum. Detailed remediation plan. Accurate timeline. Specific costs. Nothing hidden.
Multiple buyers received the same information during their competitive process. The winning bid accepted the disclosed remediation costs as part of deal structure.
No valuation surprise during due diligence. No earnout conditions tied to fixing undisclosed problems. No warranty exposure. Clean deal terms.
The alternative scenario plays out regularly. Seller assumes documentation equals compliance. Hopes buyers won’t examine products closely. Faces aggressive valuation negotiation when buyer’s technical review reveals gaps between roadmap and reality.
That path creates extended negotiations, earnout risk structures, and post-close indemnification exposure.
The Cost Math That Matters
→ Key Point: Proactive technical assessment costs tens of thousands, prevents millions in valuation adjustments
Technical assessment before entering M&A processes costs €50K to €100K depending on product portfolio complexity. Timeline: three to four weeks.
Discovering architectural gaps during buyer due diligence costs millions in valuation adjustments and months in extended negotiations or delayed close.
A manufacturing company’s compliance consultant estimated €600K and eight months to CRA certification. We examined their products. Actual engineering requirement: €2.4M and 22 months.
The gap: €1.8M and 14 months.
That gap became deal economics when buyers conducted technical review. Valuation adjustment absorbed the delta.
Proactive assessment would have cost €80K. It would have enabled accurate disclosure and prevented over €1M in surprise valuation adjustments.
What CISOs Should Ask This Week
If your company is planning M&A activity in the next 18 months and CRA applies to your products, the question from Part 1 becomes urgent:
Has anyone technically validated that your products can comply, or have you only validated that compliance documentation is complete?
Documentation review confirms your program exists. Technical review confirms your products work.
As an acquisition target: Gaps found in buyer due diligence become negotiation leverage against you. That’s deal term risk you can avoid through proactive assessment.
As an acquirer: The target’s roadmap might not reflect product architecture reality. That’s valuation risk you can quantify through technical due diligence before price negotiation.
Companies treating this seriously are examining products now, before deal processes start. Companies assuming documentation equals capability are discovering engineering reality when buyers ask to see working systems instead of compliance papers.
How KairosVector Approaches This Differently
Most CRA consultancies help you build compliance documentation and policy frameworks. KairosVector validates whether your products can technically comply with current architecture.
For acquisition targets preparing for sale:
We conduct the same technical assessment buyers will request. We identify gaps between your roadmap and product reality before buyers do. We quantify actual remediation costs and timelines. We help you decide: fix before sale, or disclose accurately and adjust expectations.
Early identification prevents valuation surprises. Accurate disclosure maintains deal momentum.
For acquirers conducting due diligence:
We examine target company products, not just their documentation. We validate whether their compliance roadmap reflects technical capability or documentation effort. We quantify remediation costs if architectural gaps exist. We provide technical findings that support valuation negotiation.
Our assessment protects you from post-close surprises that become indemnification claims.
What we don’t do:
We don’t assume roadmaps are accurate without validating technical capability. We don’t review only documentation without examining products. We don’t estimate timelines based on policy work when engineering reality determines actual cost and schedule.
What’s Coming in Part 3
Next week we’ll show you exactly what technical remediation looks like when architectural gaps are identified.
You’ll see the actual work required, not roadmap estimates. Timeline broken down by engineering phases. Costs separated into infrastructure, resources, and vendor dependencies.
We’ll explain why standard consulting approaches miss the engineering reality that determines whether remediation takes 8 months or 22 months.
And we’ll give you the decision framework for determining whether your internal team can handle assessment and remediation, or when external technical validation is necessary.
Because the difference between “we think we can comply” and “we’ve validated our products can comply” is the difference between confident deal negotiations and expensive surprises.
References
1 European Union, Cyber Resilience Act, Article 11 – Technical Documentation (Regulation (EU) 2024/2847)
2 European Union, Cyber Resilience Act, Article 47 – Conformity Assessment Procedures (Regulation (EU) 2024/2847)
3 European Union, Cyber Resilience Act, Article 14 – Vulnerability Handling Requirements (Regulation (EU) 2024/2847)
4 European Union, Cyber Resilience Act, Article 13 – Obligations Related to Support Period (Regulation (EU) 2024/2847)
For complete CRA regulatory text: https://eur-lex.europa.eu/eli/reg/2024/2847/oj
KairosVector provides CRA technical due diligence for product company acquisitions and pre-sale technical readiness assessment.
Contact us to discuss your M&A timeline and CRA technical validation requirements.